
Phishing attacks are a type of social engineering where an attacker sends a fraudulent message designed to trick a person into revealing sensitive information to the attacker or to insert malicious software on the victim’s computer or smart device and any attached networks.
Phishing is commonly associated with links in emails, meeting invites, text messages and social media direct messages which entice users to click on them. Phishing attacks are designed to get the readers attention and evoke a response quickly while ignoring the risks. Some of the attacks can be very difficult to distinguish from real emails as they use logos, names, social media links and even digital signatures to make them look authentic. However, there are so-called ‘tells’ which can indicate fraudulent content such as mis-spelling, links to untrusted sites, unexpected nature of the email or text and even timestamp of when it was sent.
6 Types of Phising
Email Phishing : Garden variety phishing where a generic email is sent indiscriminately to people on a mailing list or a company domain.
Spear Phishing : A more target form of attack where known details about a recipient are used to get their attention and encourage them to act.
Whaling : Similar to spear phishing but focused on senior executives in the company, often with the objective of authorizing fund transfers.
Vishing : Where voice/VoIP calls/messages are used to attack victims. Such as voicemail with instructions to call your bank because of a security issue.
Smishing : Phishing based on text (SMS) messages.
SEO Phishing : When cybercriminals use search engine optimization to appear as the top results on a search engine in an attempt to lead searchers to a spoofed website.
Spear Phishing
Sometimes hackers will target employees very specifically to steal funds or information or inject malware. Hackers may find information about the organization you work for, your role and personal interests on social media type sites. They can then use this information to craft an email that uses one or more pieces of your personal information to greater effect.
An example of this might be if you’re interested in golf, an email to you directly with free golf lessons from a pro might persuade you to click on a link to find out more.
Another example known as CEO fraud, targets employees with a ruse of asking them to do something urgently like approve a funds transfer. The email looks to be from the CEO of the company which lends false authority to the request.
Of particular value to spear phishers are employees with financial or CxO roles who are more likely to have access to sensitive information or the ability to transfer funds more easily in organizations.
AI is expected to accelerate these types of attacks in the next few years under the umbrella of AI-BEC (Business Email Compromise) making it even more of a headache for security teams.
Smishing
Attackers commonly use SMS messages to attack cell phones and other smart devices with SIM cards. These attacks are sometimes referred to as Smishing and can be just as effective as email in stealing information and injecting malware onto the network.
The most common types of fraudulent texts relate to deliveries, bank alerts and online subscriptions to companies like Amazon, Microsoft, Netflix etc. This is by design, as the majority of the population has one or more bank accounts and subscriptions to the above companies.
Mobile device users need to ask similar questions as with suspicious emails.
■ Is the text expected?
■ Is there a false sense of urgency being created here to get me to do something?
■ Is there spelling mistakes, was it sent in office hours?
And remember, even if the sender’s phone number looks legitimate doesn’t mean that it can be trusted. Hackers can easily clone telephone numbers to make the sender look authentic.
SEO Phishing
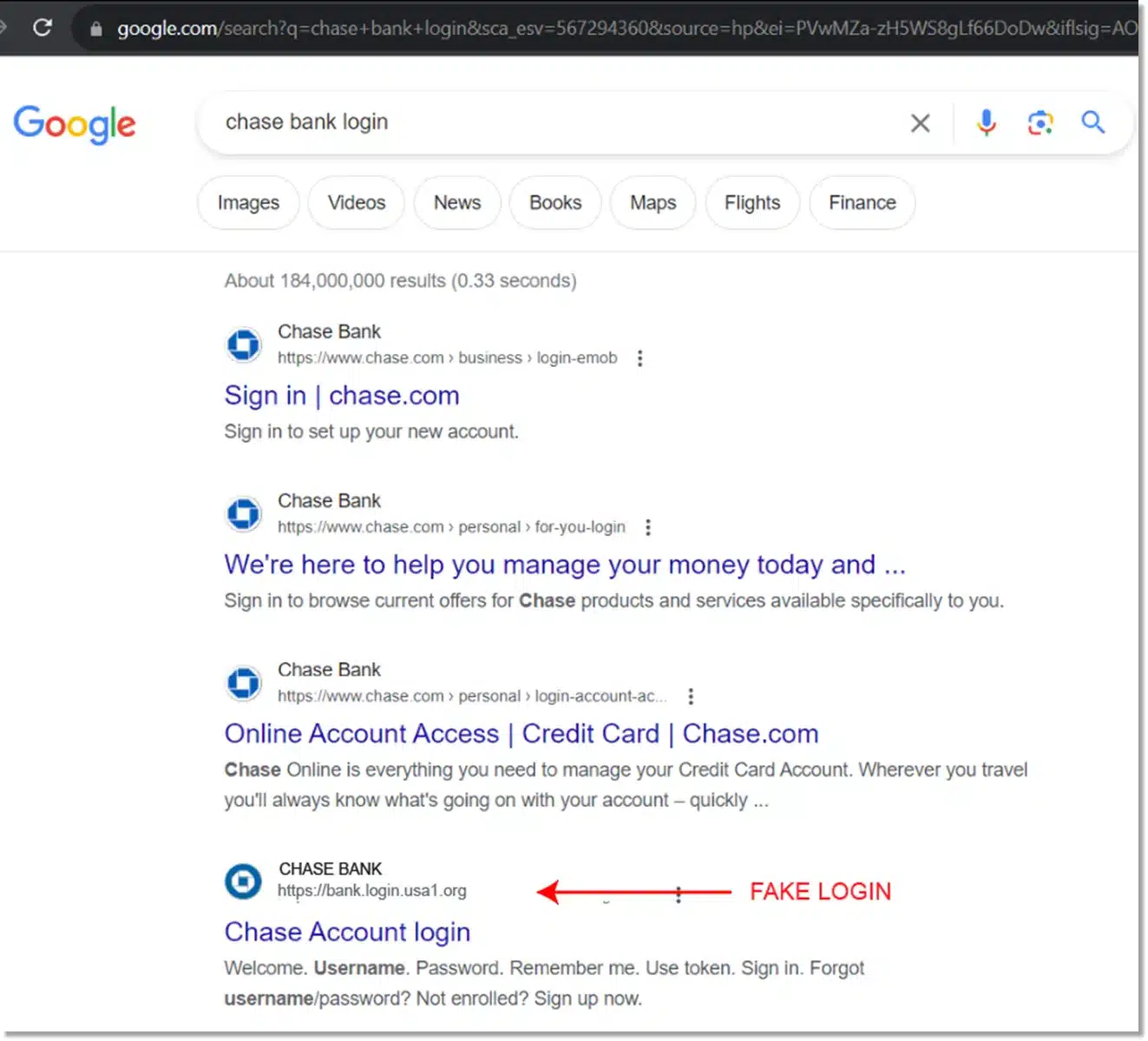
SEO Phishing Example
SEO phishing is an attack where fake websites are created (often using AI) with fake profiles and then manipulated with key search terms to rank the fake site above the authentic site on search results. This can pose a serious threat to brands as search engine results pages (SERP’s) can list malicious sites above legitimate ones. These cloned sites may collect login credentials, cause identity theft and generate company disinformation. Unsuspecting users may easily be fooled by lookalike logos and meta descriptions.
PDF Downloads
PDF email attachments are now the most common form of introducing malware to organizations. With 2/3rds of attacks starting with a downloaded PDF attachment. Users may not be aware that malicious code, encrypted files and malicious URL links maybe embedded in PDF’s. Malware is often quietly introduced via this method causing huge impact on businesses in terms of business interruption, theft of customer data and investigations. Email users can easily be tricked as most PDF’s in the workplace are legitimate.
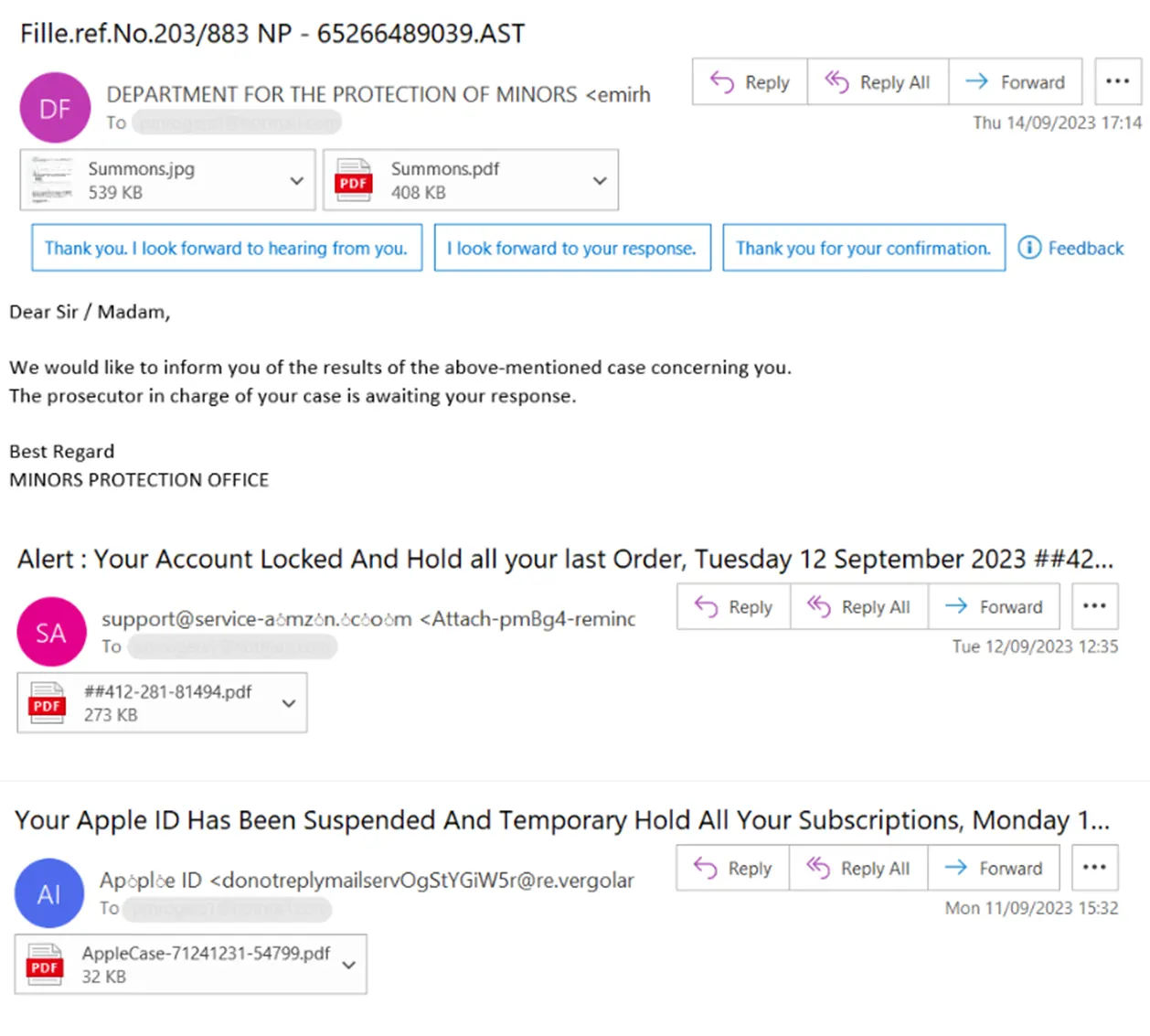
Malicious PDF Attachment Examples
6 Impacts of Phishing
Phishing attacks have increased 50% over the last 4 years globally partly in response to Covid-19. One of the most visible impacts to organizations is the effect of ransomware which is plaguing businesses globally. Ransomware is typically downloaded through malicious links in emails where it begins to infect other machines by stealing information and encrypting data. Once the data is encrypted (and thereby made unusable) Cybercrime gangs threaten organizations with releasing stolen information and locking files permanently. The FBI estimates that ransom demands in 2023 are now averaging $5.3m while there were over 236 million ransomware attacks recorded last year.
Organizations face a wrath of repercussions once infected in addition to paying the ransom if they decide to do so. Extended business interruption is common, along with investigations, customer identity theft, reputational damage, lost revenue, lawsuits, layoffs and even company closure in some cases. Often this is a result of one employee clicking on a link.
Next Steps
Training staff on the risks from phishing and other threats is a key preventative control against cybercrime. Discover our range of presentation training solutions and tools on our online store. We have low cost slideshow training on Phishing, Remote Worker Security Awareness Training, Data Privacy Awareness Training, Cybersecurity Awareness Training and more. Click the link below to visit our store or contact us on the contact us page to ask a question.
