
Yet another compliance deadline is fast approaching as the Digital Operational Resilience Act (DORA) will be enforced on Jan 17th 2025. For those of you who are still searching for answers we’ll try and explain the common ones and help you with an implementation plan.
What are the 5 Pillars?
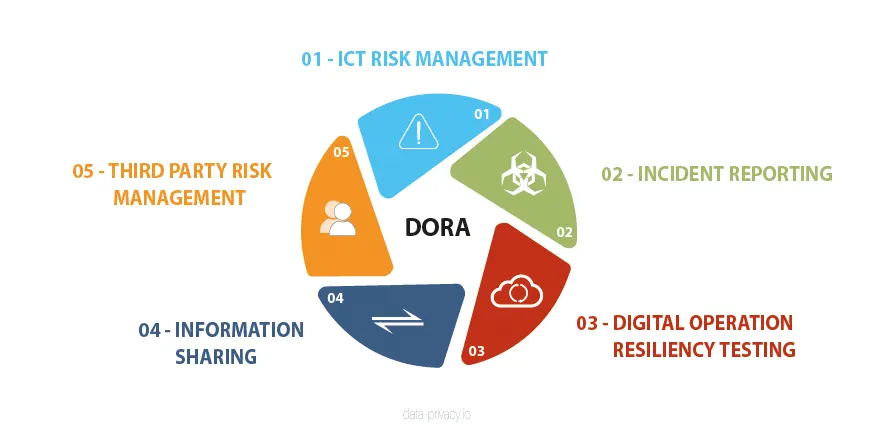
DORA includes 64 articles which are categorized across 5 domains which apply to all types of financial institutions (except micro enterprises) and their ICT providers in the EU. This includes traditional financial entities, like banks, investment firms, credit institutions, and non-traditional entities, like crypto-asset service providers and crowdfunding platforms.
ICT risk management gets the most attention in DORA regulations by far as it includes requirements for; an internal governance and control framework that ensures an effective and prudent management of ICT risk. The pillar calls for a management body to oversee its implementation and ensure periodic reviews of BCP and audit plans. The management body should implement a risk management framework which includes strategies, policies, procedures, ICT protocols and tools that are necessary to duly and adequately protect all information assets and ICT assets. ICT-RM also calls for detailed backup policies and procedures, with restoration and recovery procedures and methods which must be defined.
The Incident reporting, information sharing and 3rd party risk management pillars map closely to ISO 27001 objectives while the resiliency testing maps closely to ISO 22301 (BCP planning). An interesting detail on the BCP pillar is a requirement for annual TLPT (Threat Level Pen Testing or Red Team Testing) which exceeds NIS2 or GDPR requirements.
What are the Benefits of DORA?
While DORA maybe seen as an extra regulatory burden to most, there are a number of benefits which cannot be overlooked, some of these benefits include;
- Verification that digital environments are indeed resilient from cyber threats and operational outages.
- Mitigation of risk through valuable exercises such as threat level pen tests and other risk assessments.
- Demonstration of trustworthiness and confidence to customers and affiliates in that a robust EU wide regulation is being adhered to.
- DORA compliance can be used as a tool for FS firms to bring their ICT suppliers up to a minimum standard of security and resiliency.
- It promotes a culture of risk management in the organization as DORA objectives revolve heavily around a RM framework.
- DORA compliance is a further layer of data protection assurance over existing regulations such as GDPR and PCI-DSS 4.0.
How do I Best Comply with DORA?
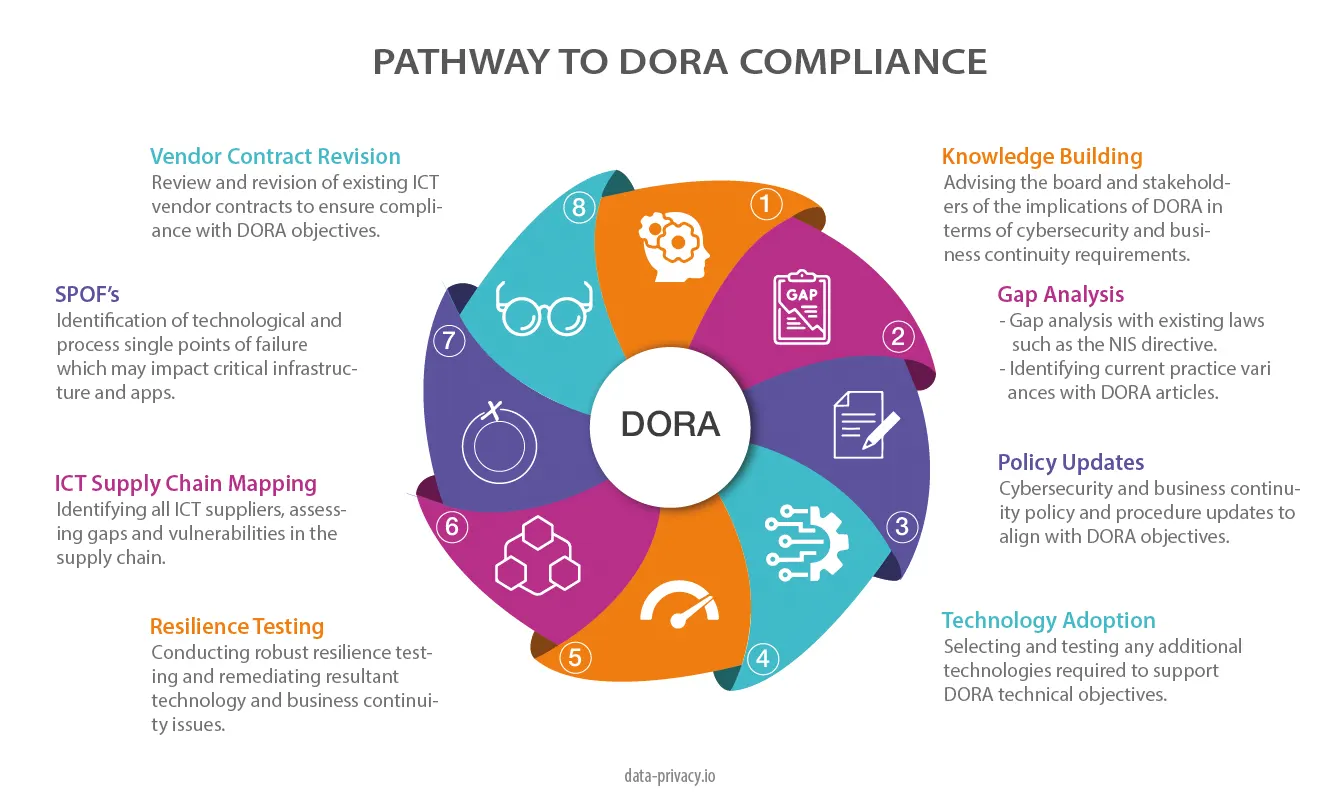
DORA compliance can best be implemented in an 8 step process, which we can see from the chart. This process starts at the top with a knowledge building exercise with the board and heads of business. The purpose here is to inform and get an executive sponsor on board to drive the compliance efforts who can approve costs and resource allocation.
The next step is a gap analysis with existing compliance activities. DORA has a strong focus on 3rd party risk management and business continuity with additional requirements around red team exercises and effective adherence to a continuity framework like ISO 22301.
The remaining steps include;
- A review of cybersecurity and business continuity policies.
- Identification and acquisition of new technology to support DORA compliance.
- A fresh round of resilience testing to cover all critical infrastructure and apps.
- ICT supply chain mapping. This step involves identification of all ICT suppliers and asessment of gaps with the security / resiliency posture of their environment vs yours.
- SPOF’s or single points of failure. This step involves the assessment of technological AND process redundancy issues such as tasks which are dependent on one person or system.
- Vendor contract revision. FS firms need to assess existing contracts against DORA objectives and update them accordingly.
With a global surge toward AI adoption, the risks grow larger heading into 2024 and beyond which means that development efforts must carefully factor in laws of unintended consequence when designing applications.
How does DORA align with GDPR & NIS2
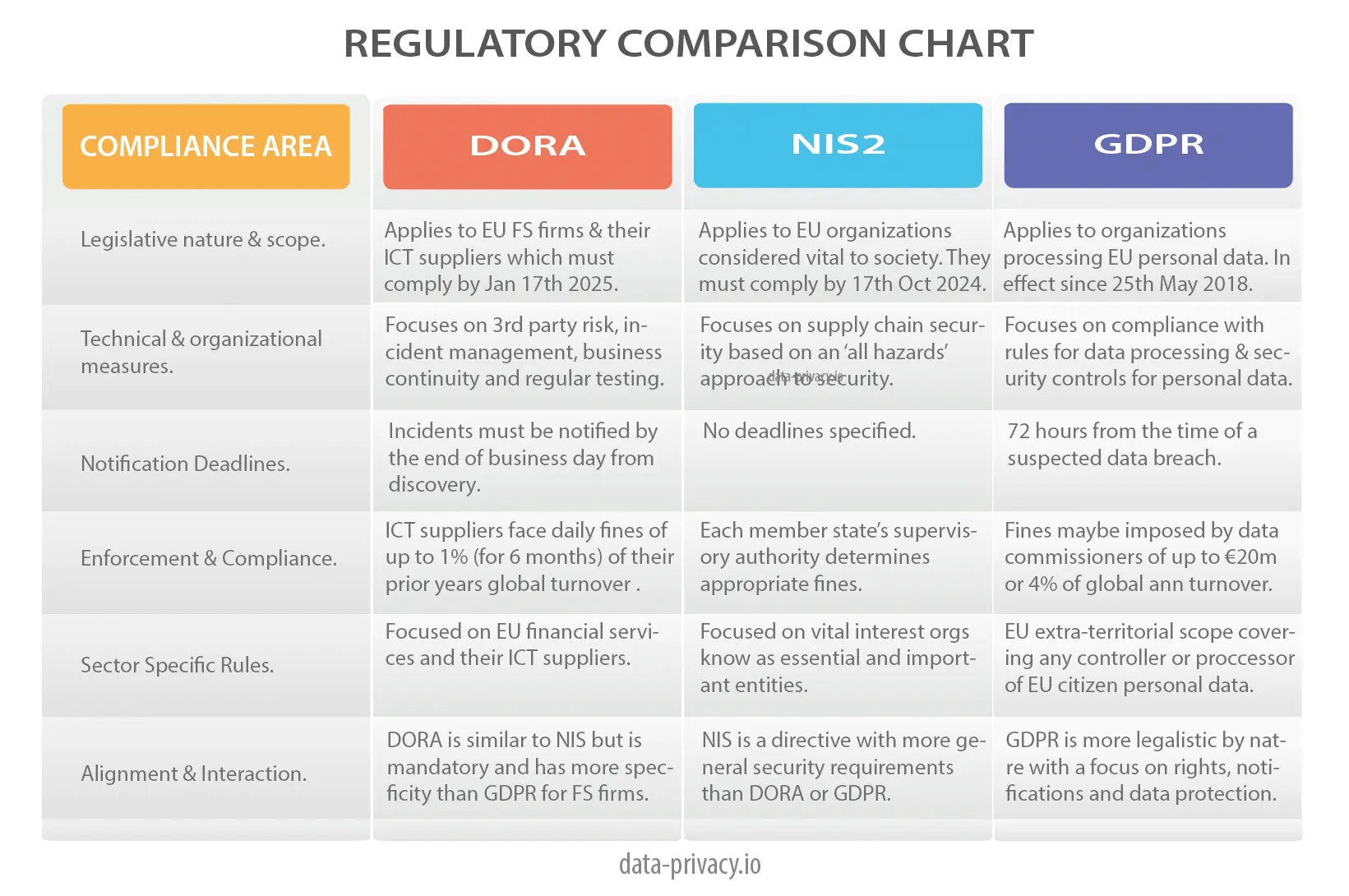
DORA largely supersedes NIS2 and compliments GDPR. The main difference revolves around the target market for each of the regulations. DORA targets EU financial services organisations and their suppliers. NIS2 targets societal vital interest organizations known as essential & important entities. GDPR targets organizations that hold personal data on EU citizens in and outside the EU.
Reading the chart, you can see specific differences across 6 areas.
What are the DORA Competent Authority Enforcement Powers?
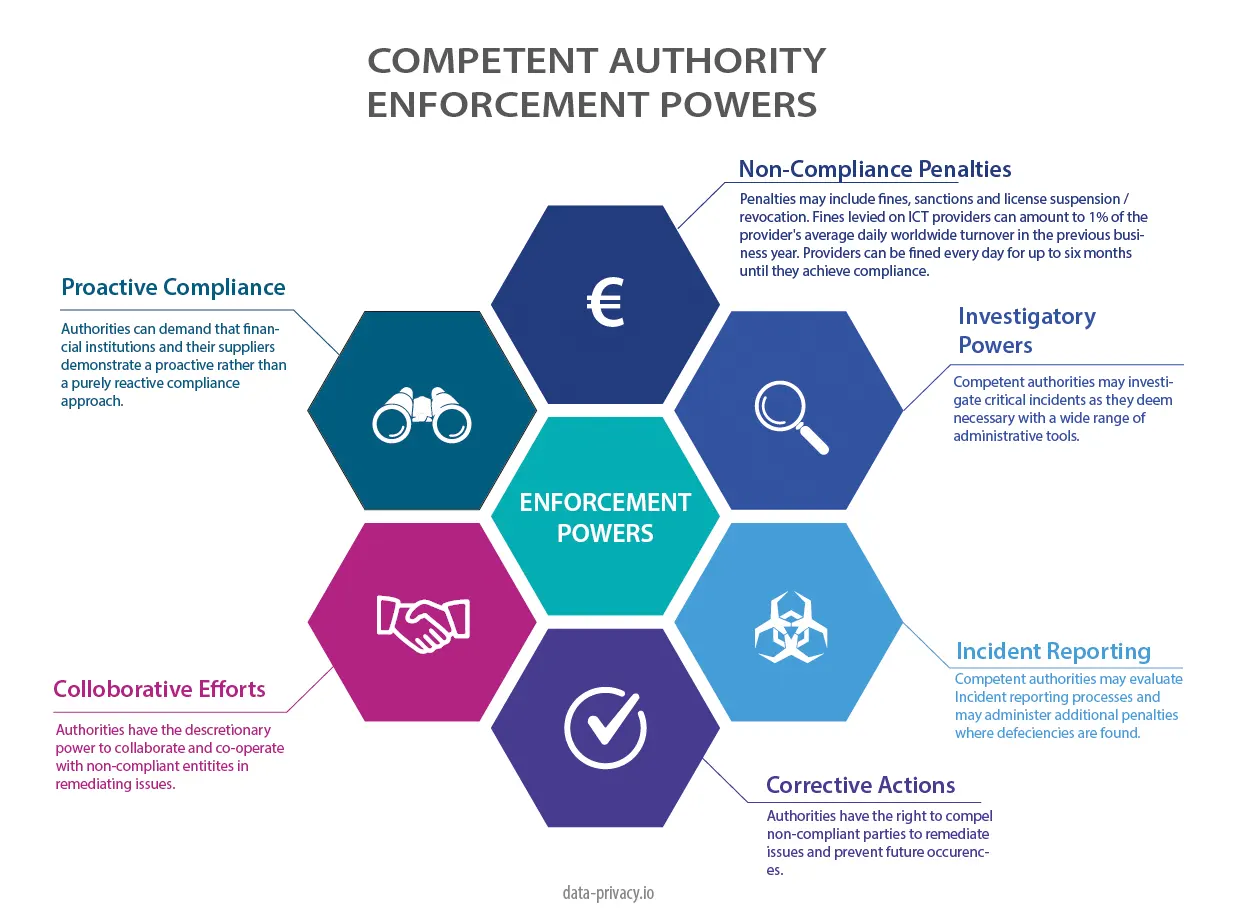
DORA delegates enforcement authority to national supervisory authorities known as competent authorities. This operates in a similar way to information commissioners under GDPR. The only definite fine is proscribe for ICT suppliers who are deemed to breach DORA regulations. This includes a fine of up to 1% of the suppliers average daily worldwide turnover for the prior year. They can be fined daily for a period of up to 6 months until compliance is achieved.
Want to find out more about DORA, checkout our Introduction to DORA presentation by clicking the image below.


Leave A Comment