
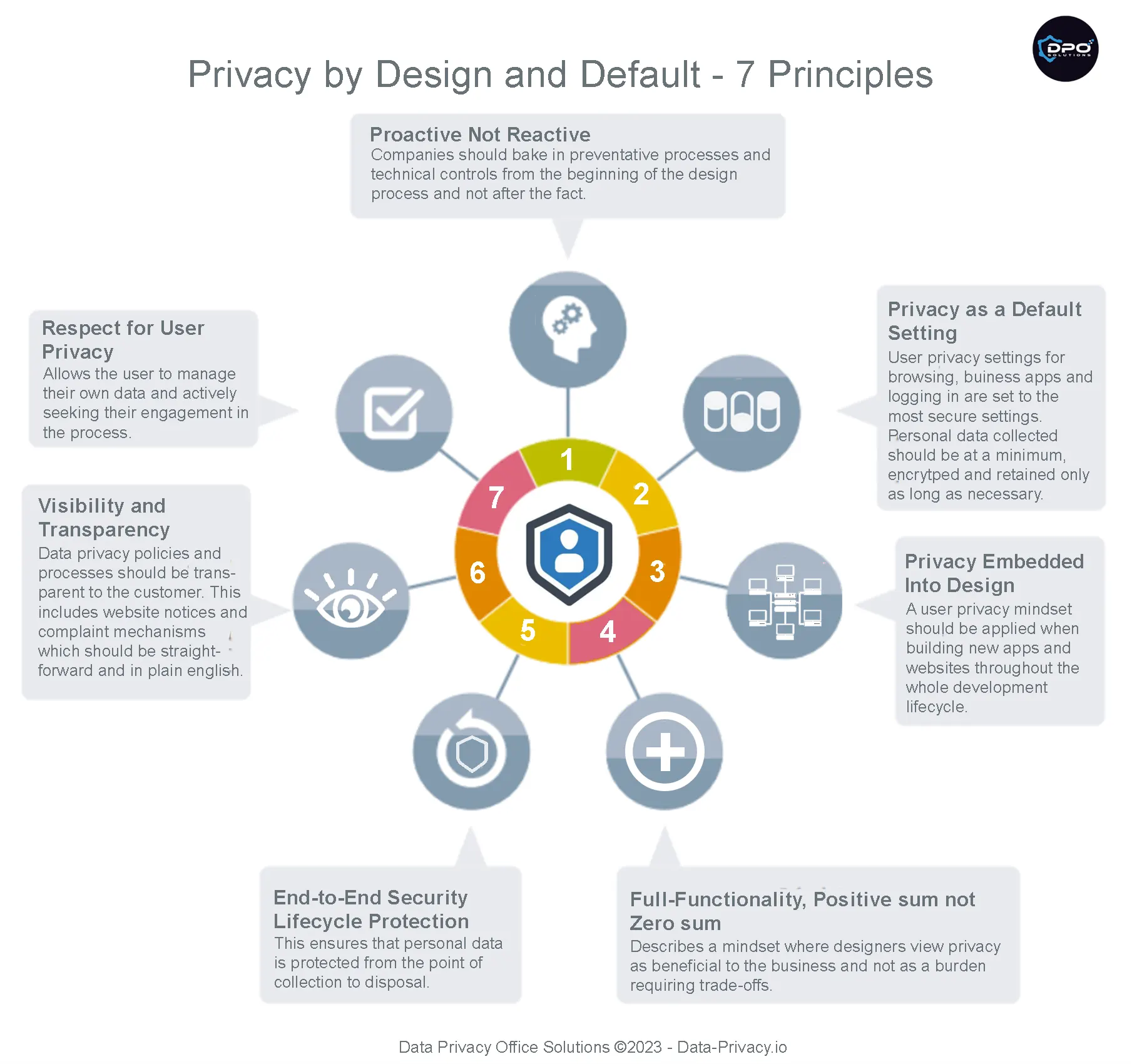
Implementing the 7 principles of privacy by design is perhaps the most important step for companies looking to comply with GDPR and other privacy laws but can also be the most challenging. Privacy laws are high level when it comes to implementation guidelines and non prescriptive in what technologies or processes to use. It’s therefore important to have a detailed approach to compliance founded in best practice. Here are a couple of guidelines to make sure you’re on track.
What encryption should I use for privacy by design Controls?
Encryption is a universal requirement for privacy by design objectives, an important thing to remember is using the latest standards. For example wireless encryption standards have moved to WPA3, while TLS v1.3 has replaced earlier versions of transport layer security. For data at rest, ensuring that the latest TDE version is used on Azure SQL databases or Oracle database is equally important. Vendor management platforms like Azure Sentinel and vulnerability scanners like Acunetix should be leveraged to keep an eye on encrpytion levels across the enterprise as regulators will expect due diligence when keeping encryption up to date. Automated key management systems such as TKLM for IBM Tape libraries, AWS KMS and Azure key vault should always be used over manual methods. The overhead factor of manual management creates a vulnerability when keys are stored outside a secure system and are not rotated.
A best practice for removable devices like laptop hard drives is to also to use managed whole disk encryption. This can be important in the recovery of data from a hard drive when a user has left the company or a forgotten passphrase.
How do I achieve transparency in processing?
The primary method for achieving transparency is through online notices to consumers. GDPR requires that consumers must be informed of what personal data is being used, who it’s share with, why it’s being processed, how long it’s needed and the legal basis for collection. See our Sample Online Policy for our example. Giving consumers over how their data is processed supports the transparency requirement and is increasing automated through consent management platorms (CMP’s). These platforms facilitate consent preferences being honored across multiple channels. In practice, this could mean that a customer opts out of any kind of sharing their data on a business website and their decision would be respected across email and subscriptions to social media accounts.
What privacy access controls should I use?
Access controls are a key method of segmenting networks and restricting access to authorized personnel. The precursor to successful access controls is network and application documentation. Interface points between where personal data lives and non personal data needs to be delineated. Application and database level access controls should be managed at at a very granular for privileged access to personal data. In addition to the normal security groups, network access lists on switches, firewall rules, mac filtering and so on, there should be also a focus on API security. SOAP and REST have different implementation of security but need to be considered in most enterprise environments. Techtarget does excellent coverage of API security and their requirements. Logging of API calls supported by traffic rate limiting and TLS encryption are a key element of API security.
How do I keep up to date on privacy risks?
Knowing where to monitor privacy risks is an important part of keeping on top of potential problems. Every year privacy reports and lists of violations are issued by EU data protection authorities such as the Irish DPC and the UK ICO along with incidents from ENISA (European CSIRT) and cybercrime reports from Verizon, FBI-IC3 and the Ponemon Institute to name a few.
From a application perspective OWASP’s Top 10 privacy risks and countermeasures combined with the aforementioned Techtarget link in the previous secction.are important guides for devops teams in the secure development process.
How do I enforce data minimization?
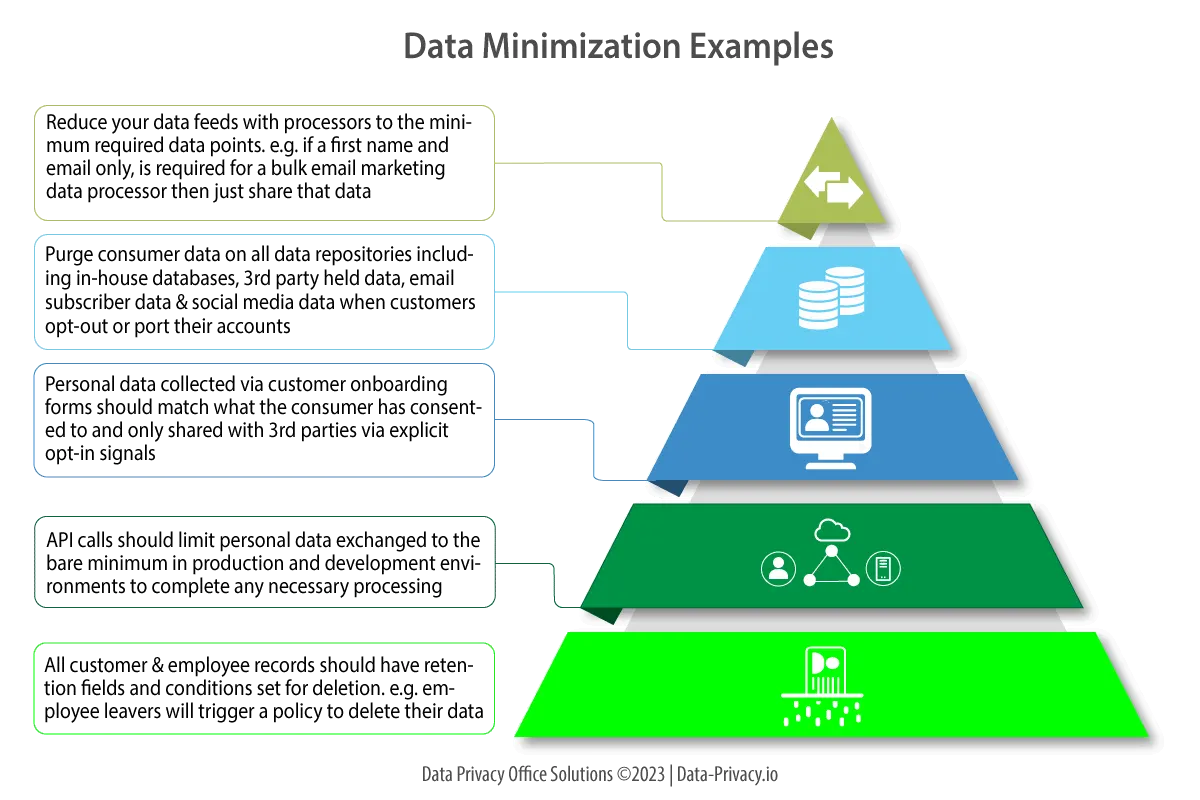
Data minimization is focused on reducing attack surface and unintended data leakage. These areas should get particular attention in the development and marketing functions as these functions deal heavily with embeding privacy controls and data collection.
Developers need to think about reducing information shared in data feeds and application API calls. One example of data minimization might be a business marketing dept who uses Mailchimp for bulk email processing. Mailchimp handles mass marketing emails for the businesses customers based on a realtime feed from data collected on the business website. Emails in this case will likely require only a first name and email address for Mailchimp to process them, hence the marketing dept need not send customer last names or any other information in the data feed to Mailchimp. This will minimize the severity of a data breach should Mailchimp be hacked at any stage.
Data minimization also means holding on to data for the minimum required period so as to keep compliant with it’s legal basis of processing. An example of this might be customer personal data which has been collected on a business website for the purposes of a customer satisfaction survey. After the survey data has been compiled, it may be unlikely that the personal data needs to be further retained hence it should be deleted. The diagram below shows some other examples to help illustrate best practices when minimizing data use.
How do I achieve data transparency?
Data transparency is intended to inform consumers about how their personal data is going to be used at or before it’s collected. This will allow customers to make an informed consent decision when deciding whether their data is appropriately processed and shared. For all intents and purposes, tranparency really means that when a customer is about to enter their information on a business website form, or sign up for a service or fill out a paper application form, that they are told in simple terms how their data is being used.
The onus is very much on the business in being truthful at the peril of being srutinized down the road, after a breach for example. Case in point, if a business collects the personal information and forwards it a sister company for the purposes of lead generation and that sister company is later breached then there could be a problem, if this processing wasn’t disclosed. Several class action attorneys and FTC officials have litigated cases when incidents like I’ve just described have happened.
What is end to end security lifecycle protection?
This is a key part of the privacy by design principles and is really a catch-all for privacy designers by posing the question, have you thought about protecting the flow of data from collection to disposal. Another way of asking the question is have you thought about protecting personal data in transit and at rest with respect to technical and administrative processes. Frameworks such as NIST’s SP800 series, ISO 27000, CIS Benchmarks, PCI-DSS and OWASP privacy controls will encapsulate most of the required controls for this principle. From a privacy technical standpoint, think
- Encryption of data stores, removable media and communication protocols (HTTPS, WPA3, TLS v1.2+, OpenSSH 8.8+)
- Access controls (Network access lists, MAC filtering, VPN security groups, firewall rules, domain groups)
- Data Loss Prevention (covering the four main architectures endpoint, network, cloud and discovery)
- Logging (Database access event logging, network and cloud priviledged account access monitoring, web server event logs, API call logging, remote access logging)
- Vulnerability management across the entire estate and 3rd party processors
- Source code review tools (e.g. Veracode) and privacy security review gates at each stage of the development lifecycle which cover major areas like form input validation, API security (REST/SOAP etc) and access controls.
From a privacy administrative control standpoint
- Implementation of a data retention policy implementation for all customer PII across all company channels
- Personal data breach policy with defined roles and responsibilities, notification templates and post incident ‘lessons learned’ components (see our Breach notification template)
- Privacy impact assessements for any GDPR/US law in-scope systems (see our PIA template) and guide to performing one
- Maintenance of an up to date record of processing activities (see our ROPA template)
- Media disposal policies (magnetic, printed and optical media)
How to Perform a DPIA | DPO Solutions
Privacy impact assessments are required under GDPR Art.35 and US State privacy laws. Learn the steps required for a PIA and download our template.
Steps to Performing a ROPA
Learn how the steps to maintaining a ROPA to meet your privacy obligations
Job Prospects in Data Privacy are Looking Brighter Than Ever
Career prospects are looking good for professionals pursuing a career in data privacy. In this article we'll look at the opportunities and salaries you should expect to see in 2024.
Phishing Security Tips for 2025 | DPO Solutions
3% of all email is malicious across the globe. Follow our tips on how to keep your personal and work email safe in 2025.
Best Privacy & Security Certifications in 2024
Privacy and Security Certification is set to be another hot item in 2024 but which one should I go for and why?
DORA Regulation Primer
The DORA compliance deadline is fast approaching. Understand what the 5 pillars mean and how to implement a compliance plan.













Leave A Comment