 |
 |
Introduction
The 2020 Verizon Data Breach Investigation Report (DBIR) has been released and is as always chock-full of sobering facts about cyber security or rather, insecurity. This report is a yearly barometer of where cyber security weaknesses lay most exposed and by extension where market vertical stakeholders should focus their efforts. The volume of research involved is significant and the defined methodologies for incident metrics, classification and controls is equally significant. In this article I’ve chosen a few facts covered in the report and expanded on the depth and impact to corporate and non-corporate end users. I’ve also put in some remediation recommendations and linked to other pertinent articles that I’ve written and external reports.
Incident Classification
The first thing that struck me while reading the Verizon DBIR report is that that many companies have problems classifying incidents and breaches given that of the 157k incidents reported to Verizon researchers, 32k were deemed to be actual incidents and about 4k were actually deemed to be breaches. Verizon makes mention of a “quality control” screening process and refers to a Veris and the Mitre Attack Frameworks framework for incident classification. It’s worth considering that firms may want to look at their own incident classification policies and procedures and ensure that they are aligned to an established framework which is a better fit for purpose.
Financial Motivation
Unsurprisingly financial motivation is the primary motivation for attacks this year and every other in the Verizon data breach incident report series. A browse through the dark web markets and interviews with hackers will quickly convey this fact as well. The cyber security firm Sixgill, which monitors dark web marketplace activity, found that 76,230,127 compromised cards were offered for sale in the markets in the second half of 2019. This is up 200% from the 23 million in the first half of the year. The average price for a stolen US credit card was in the neighborhood of only $11 while a UK card was £25. Now have a look at the graphic below for the bigger picture.
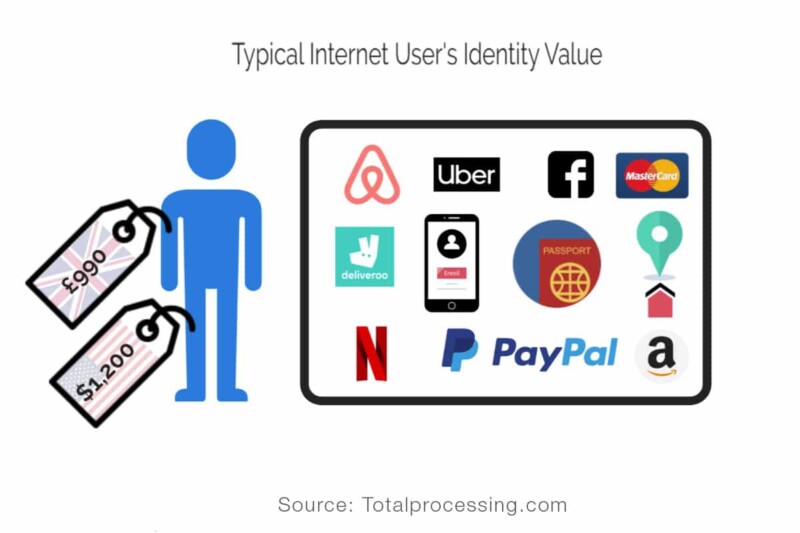
The average person has many online account types ranging from social media to email and online shopping platforms etc. Add up all of those accounts and the typical internet user’s identity is worth about $1,200 or £987 to hackers. Many hackers admit (via encrypted chat channel confessionals) to making upward of $20k per week in selling identities, cards, hacking services, PhaaS (Phishing as a Service) etc. Many of them also operate with relative impunity from the usual suspect territories such as the Russian Federation. Russia’s FSB (Federal Security Service and the Russian Ministry of Internal Affairs have notoriously given a pass to hackers targeting entities outside their jurisdiction. Of course, they do have their minimum standards. i.e. don’t hack where you eat. Case in point below;

BuyBest Bust: Mar 2020 Russia Charges 25 Individuals With Trafficking in Stolen Bank Card Data (Within Russia)
Fact of the matter is that over 55% of breaches are committed by organized criminal gangs and remembering that a cyber gangs very raison d’etre is to make money.
Email: Friend and Foe
The term phishing appears 74 times in the Verizon DBIR report while the term BEC (business email compromise) appears 10 times in the report. It would seem that until the industry rolls out an affordable “Deep Blue” like chess computer technology to challenge would be adversaries, it will the most effective and easiest method for attackers to monetise their efforts. This topic set me thinking, and just for fun I decided to run an identity theft checking tool from F-Secure to check how compromised my personal email address is.
It seems that my email has shown up in 12 breaches over the years. Linkedin and Adobe breaches being the most notable ones. I was surprised but then again not, having looked at big firm breach history over the last 10 years. I would encourage anyone to check their own email, change their passwords to a different strong password for each online account and enable 2 factor authentication (2FA). Various vendors offer password managers as human assist tools to help you store complex passwords. Look for ones that backup to the cloud in case your PC becomes unavailable.
It’s been said in forms of slight exaggeration that “If someone solves the phishing problem, 99% of cyber attacks will be mitigated”. Well if they throw in human error and webapps, I’d completely agree. In any case the level of effort and cost is low to launch phishing attacks, online phishing kits, banking and social media lookalike email templates are available for under $30 or (0.0032 Bitcoin) at today’s rate (if your buying: joking). The next section I’m going to devote to phishing mitigation as it’s such an important topic.
Corporate Phishing Mitigation Strategies (from the digital shadows report and Banksecurity.com)
- Limit the information your organization and employees share online, including on social media sites. The most successful phishers perform detailed reconnaissance so they can craft the most effective emails and social engineering lures.
- Monitor for registrations of typo-squatted domains that attackers can use to impersonate your brand, send spoofed emails, and host phishing pages.
- Implement additional security measures, such as Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM). These can make the spoofing of your domain more difficult.
- Protect your accounts in case phishers do manage to steal user credentials. Two-factor authentication measures should be mandated across the organization and implemented whenever possible.
- Train your employees how to spot phishing emails and, more importantly, give them a clear and recognized reporting method to alert security teams of suspected phishing attempts. Eventually, a phishing email will fall through the net. Employees need to know how to react to these quickly and should not fear any repercussions of being the victim of a social engineering attack.
- Encrypt internal email as well as external email services The five most common technologies that have led to accidental data breaches by employees, according to a recent survey by opinion matters research group, are external email services (51%), corporate email (46%), file sharing services (40%), collaboration tools (38%), and messaging apps (35%). The research also shows that 79% of organizations share sensitive business data internally without encryption, and 64% share sensitive business data externally without encryption.
Errors
As reflected in the Verizon DBIR, errors and webapp type breaches share top spots for breach causality in the financial services sector.
I can fairly understand why webapps are a top source of breaches given the complexity of securing them but, to share the top status with human error is a little more beguiling. The report does mention that a lot of error is detected through security researchers rather than hackers but nonetheless, obvious mistakes are being made.
I’ve touched on insecurity in email services in the last section but it’s important to understand the most common email accidents that lead to data breaches which is not completely covered in the report. These are accidental sharing/wrong email address, email forwarding of sensitive data, sharing attachments with hidden content, and forwarding data to personal email accounts. Can anyone say encryption again.
No less significant than email errors, is the internet storage mis-configuration category. As a lot of storage is now hosted on the cloud may I recommend my article on 10 steps to securing the cloud as a suggested read.
In case you don’t have time to read that, I can summarize by saying protect encryption keys, make sure storage visibility is not set to public unless it’s really supposed to be, set restrictive permissions on objects and conduct audits of your cloud and on-prem estate. Pay attention to CSP container objects and NFS shares. Most CSP’s have their own auditing tools like AWS’s Trusted Advisor or Microsoft’s Azure Security Center which can help identify insecure conditions.
There is of course another causality for human error which is a little bit more of a human problem than a technical one, I make mention to it in my aforementioned article on 10 steps to securing the cloud and that is
Culture Creep:
The question then becomes (as it relates to breaches), why are these things happening and what can I do? In my experience culture creep often skews all your best efforts to address security problems. Silo’d departments, poor practices of not documenting what you have particularly in a fast paced agile application development world, security perception as an inhibitor within an organization and more. This leads me to the next section Asset Management which is interconnected with poor documentation.
WebApps
It’s fair to say that there’s an IT migration to service oriented architecture (SOA), more specifically cloud based SOA. Unfortunately with great convenience comes greater risk, a lot greater. The more public nature cloud hosted services has meant a greater attack surface. It really is more important than ever. I’m going to quote from my own article here that mostly applies to cloud services but can be applied to on-premise web services as well.
Enterprise Security Architecture
“When thinking about security architecture, there are many avenues to go down in terms of a adoption of a defense in depth approach. Given that 40% of breaches are related to insecure development code (Verizon DBIR 2019) being hosted on cloud based servers, I think it’s a good place to start this topic.
SANS Analyst David Shackleford tells us in his article entitled The DevSecOps Approach to Securing Your Code and Your Cloud that only 17% of infosec organizations can keep up with continuous or agile development. He promotes seven imperatives for security teams, the top 4 of which I’ve included here. 1) Embedding security controls and automation in code developed in the cloud 2) Inventory and analysis of reusable code to avoid re-introducing flaws 3) continuous monitoring of code and results in production & 4) creation of “triggered” responses that can roll controls back to a known good state if there’s a problem. Following some other of Dave’s good advice on architecture in his Youtube presentation “A Cloud Security Architecture”, he advises us to think about cloud security controls and tools which should not be designed with one CSP in mind. The reality is that many organizations will be not just be an AWS or Azure or GCP shop, they will likely follow a hybrid model through accident or design. So when designing IAM security policies for example, consider their application across multiple CSP platforms so as not to get locked in to one provider. An alternate approach is to leverage security broker services or CASB’s which are offer for managed security policies across multiple platforms.
Of course with any good security architecture we have to think about designing for availability or designing for failure as it’s often referred to in the cloud. At the application level a few pointers would be for developers to make no assumption about the reliability of the underlying infrastructure thus adaptability should be paramount. It also holds true that each application component must be designed across multiple cloud components and automation tools must be in place to allow applications to respond to infrastructure failures. Specific types of failure recovery objectives might be, recovering from a bad server image deployed across the EC2 environment or recently deployed security group definitions which are too permissive and need to be rolled back. You will also need to consider potential elasticity failure issues such as bad load balancing parameters which fail to scale up applications when needed.
These points only touch on overall security architecture of a cloud environment, the point here is to get the imperatives right and embed security failure scenarios in every infrastructure and application component in the cloud.”
Asset Management
The DBIR report makes mention to the fact that given the vulnerability statistics that organizations actually know about they probably do not have a handle of what there assets are. Asset management is the grey area that hackers love to live in, unpatched hosts in the area 51’s of corporate networks. In my experience, lots of manual effort in the form of barely dynamic spreadsheets, host files on SolarWinds monitorting stations and word documents hold the grand footprints of the networks that live in your enterprise. This doesn’t have to be mapping the human genome, but you do need to be diligent in change management processes, adopt automation as a mantra. This one deserves the effort of a business critical service with a budget for resources to complete the task on a regular basis.
Financial Bottom Line
So let’s say I wasn’t really a security guy and didn’t really get a lot of the security-esque spiel of the last sections, however, I like to talk numbers though, financial numbers and I do care about the financial health of my organization.
The Verizon DBIR report does mention that email compromises typically costs firms 32k, but that doesn’t really capture the bigger picture. The truth about security is often not always as straightforward as running a P&L or Balance Sheet report in Sage. The actualized costs of a breach is not black and white perhaps ever when you factor in reputational damage. Typical costs relate to costs to fix the issues identified in the attack, communicating and compensating customers, lost revenues and sales, the associated brand and reputational damage, on-going legal costs and loss of market share. Maersk reported losses of around $300Mn and Merck of over $800Mn for the Not Petya Ransomware attacks which started in 2016. Many companies dont want to even disclose amounts or even that there was a breach in the first place, but that’s not all. There’s that regulatory ring of fire.
Regulatory ring of Fire
Lest we forget the regulatory ring of fire so to speak which is gradually encircling industries with each passing year. GDPR, California CCPA, New York Shield and others have spurred on data protection authorities and state attorney generals to start fining errant friends.

The UK Information Commissioners Office has already been busy flexing the rod which we can only expect to see more of.
Summary
In summation, this report is a useful tool that will be read by tens of thousands of stakeholders, To me, the theme of human error is the key takeaway, as it’s the most avoidable and the most harmful. Hence if I were to focus on where my next 100k was spent, it wouldn’t be next version of phablet for my staff but a multi-year training program which included targeted training for my sys admins, developers and general staff.